Data exchange encryption
In today’s digital landscape, ensuring the security and integrity of data exchange processes is most important for businesses across all industries. While current data exchange methods in Synerise involving files or HTTPS requests are secured with protocols, some organizations may require an additional layer of protection for sensitive information.
To address these heightened security needs, Synerise lets you improve the security of your data transfers by decrypting incoming data and encrypting outgoing data by RSA or AES keys which you can add in Synerise.
These keys can be used while preparing data transformation rules in the form of Encrypt Data and Decrypt Data nodes, which can help you encrypt and decrypt data in the files which you retrieve or export outside Synerise.
This feature is primarily tailored for enterprise customers seeking to secure their data exchange processes and uphold highest security standards.
Purposes
You can use RSA or AES keys for the following purposes:
| Key type | Functions |
|---|---|
| AES (265-bit keys only) | - this key type operates using AES-GCM mode, - encrypting and decrypting values in an imported/exported file, - encrypting and decrypting by means of Jinjava tags, Jinjava encrypt filter, and Jinjava decrypt filter |
| RSA (RSA-2048 standard only) | - this key can encrypt only small amount of data (up to 180 bytes), - encrypting by means of the encrypt Jinjava tag and Jinjava encrypt filter |
Logic
The process of adding the key is determined by the distinct logic provided by AES and RSA keys.
AES keys
In Synerise’s data exchange encryption process, you bring your own Data Encryption Key (DEK) to encrypt and decrypt data within our system. Synerise provides you with the Key Encryption Key (KEK) which you must use to wrap your DEK to secure the transmission of the encrypted data and to restrict access only to authorized users. This process looks as follows:
-
Download a workspace key encryption key (KEK) from Settings > Encryption Key.
-
Wrap your AES-256 secret key using the downloaded key encryption key and the Python script below. The script accepts a base64-encoded secret key, only 256 bit/32 byte secrets are supported. The script will use RSA-OAEP padding with SHA-256 to print a wrapped AES-256 key to standard output.
Click to expand the scriptfrom cryptography.hazmat.primitives.asymmetric import padding from cryptography.hazmat.primitives import hashes from cryptography.hazmat.primitives.serialization import load_pem_public_key import click import base64 from importlib.resources import path def encrypt_key(public_key, secret_key): ''' This function takes PEM encoded public key and AES secret key in base64 encoded form (raw bytes base64 encoded) and wraps the AES secret using public key. The public key for wrapping may be downloaded from UI or using Synerise API endpoint /workspace-wrapping-key and is global for each workspace. Note! As for now only 32 bytes (256 bits) secret key is supported! ''' padding_config = padding.OAEP( mgf=padding.MGF1(algorithm=hashes.SHA256()), algorithm=hashes.SHA256(), label=None ) encrypted_data = public_key.encrypt(secret_key, padding_config) return encrypted_data @click.command() @click.option('--public-key', 'public_key', required=False, help='RSA wrapping public key') @click.option('--public-key-file', 'public_key_file', required=False, help='RSA wrapping public key file path') @click.option('--secret-key', 'secret_key', required=True, help='Base64 encoded secret key to wrap and upload') def wrap_key(public_key: str, public_key_file:str , secret_key: str): ''' Script wrap_aes_key_for_synerise. Specify either: --public-key "{public-key-content}" or path to public key file: --public-key-file {path} and a secret key (base64 encoded AES-256 secret i.e. 32 random bytes) to wrap for upload to Synerise. Requires packages: "click>=8.2.1", "cryptography>=45.0.5", ''' key = public_key if public_key is None and public_key_file is not None: with open(public_key_file, 'r') as file: key = file.read() secret_key_bytes = base64.b64decode(secret_key) len_secret = len(secret_key_bytes) assert len_secret == 32, f"Secret key must have 256 bits/32 bytes! Given a secret key with: {len_secret} bytes !" # prepare PEM key from Synerise format i.e. # first prune PEM marks and construct PEM key with a prefix, 64 characters per line and pem suffix pem_prefix = "-----BEGIN PUBLIC KEY-----" pem_suffix = "-----END PUBLIC KEY-----" key = key[len(pem_prefix):] if key.startswith(pem_prefix) else key key = key[:-len(pem_suffix)] if key.endswith(pem_suffix) else key lines = [pem_prefix] while True: if len(key) >= 64: lines.append(key[:64]) key = key[64:] else: lines.append(key) break lines.append(pem_suffix) public_key_in_lines = "\n".join(lines) # load pem public_key public_key = load_pem_public_key(public_key_in_lines.encode()) # encrypt does wrap on AES DEK key encrypted_key = encrypt_key(public_key, secret_key_bytes) wrapped_key = base64.b64encode(encrypted_key).decode('utf-8') print(wrapped_key) if __name__ == "__main__": wrap_key() -
Upload the output of the above script to Synerise while adding an AES encryption key.
RSA keys
When you add an RSA key type to Synerise, you only need to provide the public key while ensuring the private key is securely stored in a safe location. This means that the process of adding the RSA key only requires providing your public key.
Statuses
An encryption key can receive the following statuses:
- Enabled - A key receives this status after creating. The key is ready for use.
- Pending - A key receives this status when it’s activation date is set for the future.
- Revoked - After being revoked, a key and its versions are labeled as revoked. A key in this state cannot be used and its status cannot be changed.
WARNING: Revoking a key used in a transformation rule within a running workflow will cause that workflow to stop working. - Expired - This status can be assigned to a key version. The encryption key version with this status cannot be used.
Requirements
You must have a user role with the following permissions:
- Settings > Encryption keys > Read - To preview list of encryption keys, preview list of encryption keys in Encrypt Data and Decrypt Data nodes in Data Transformation;
- Settings > Encryption keys > Create - To create an encryption key;
- Settings > Encryption keys > Edit - To add a key version, to revoke the key;
Adding an encryption key
The procedure involves downloading a key encryption key (KEK) which you will use to encrypt (or decrypt) your data encryption key (DEK). After you encrypt your key with the KEK, you can paste it in the form. Additionally, you can define the name of the key, add a description to the key (to let other workspace users know what is the purpose of the key), activation and expiration dates.
-
Go to
 Settings > Encryption keys.
Settings > Encryption keys. -
In the upper-right corner, click Add Encryption Key.
-
From the dropdown list, select the key type:
- Symmetric key (AES)
- Asymmetric key (RSA)
Result: A pop-up appears.
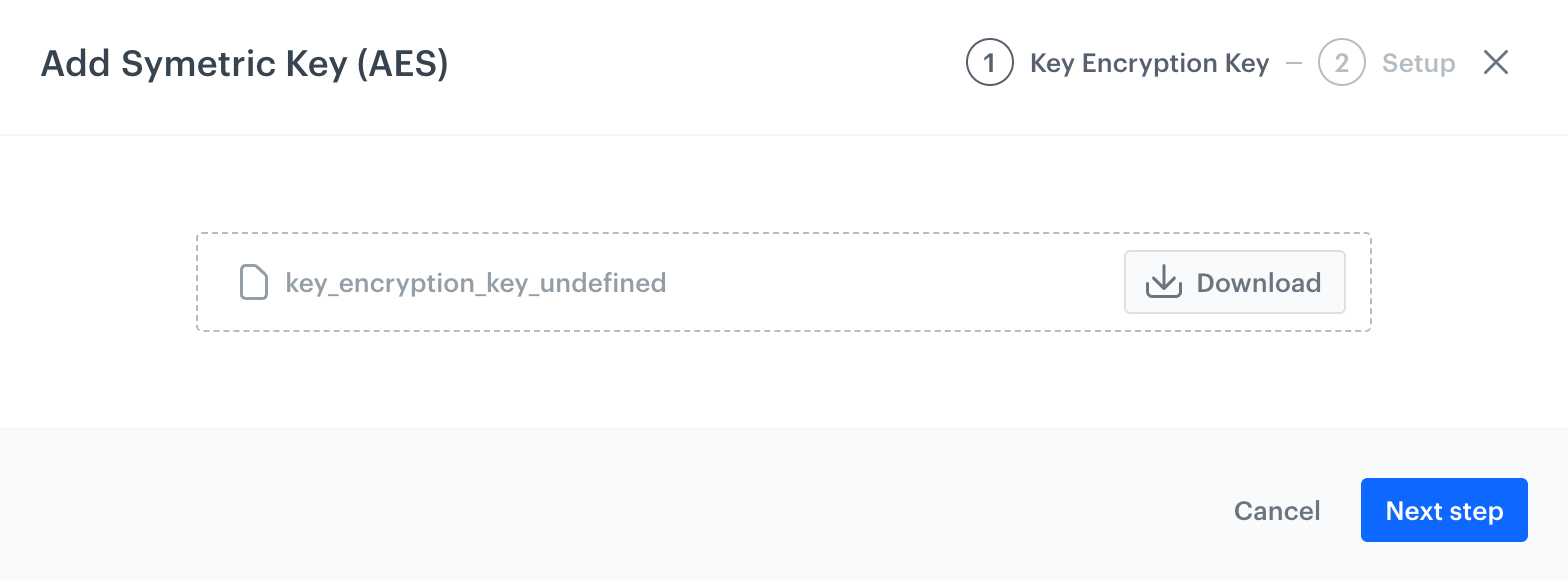
A pop-up displaying the encryption key for download -
If in the previous step:
- you selected Symmetric key (AES), click Download.
Result: A key encryption key is downloaded to your device. Make sure you wrap your DEK with this key and script provided in Logic for AES keys. - you selected Asymmetric key (RSA), click Next step. Result:
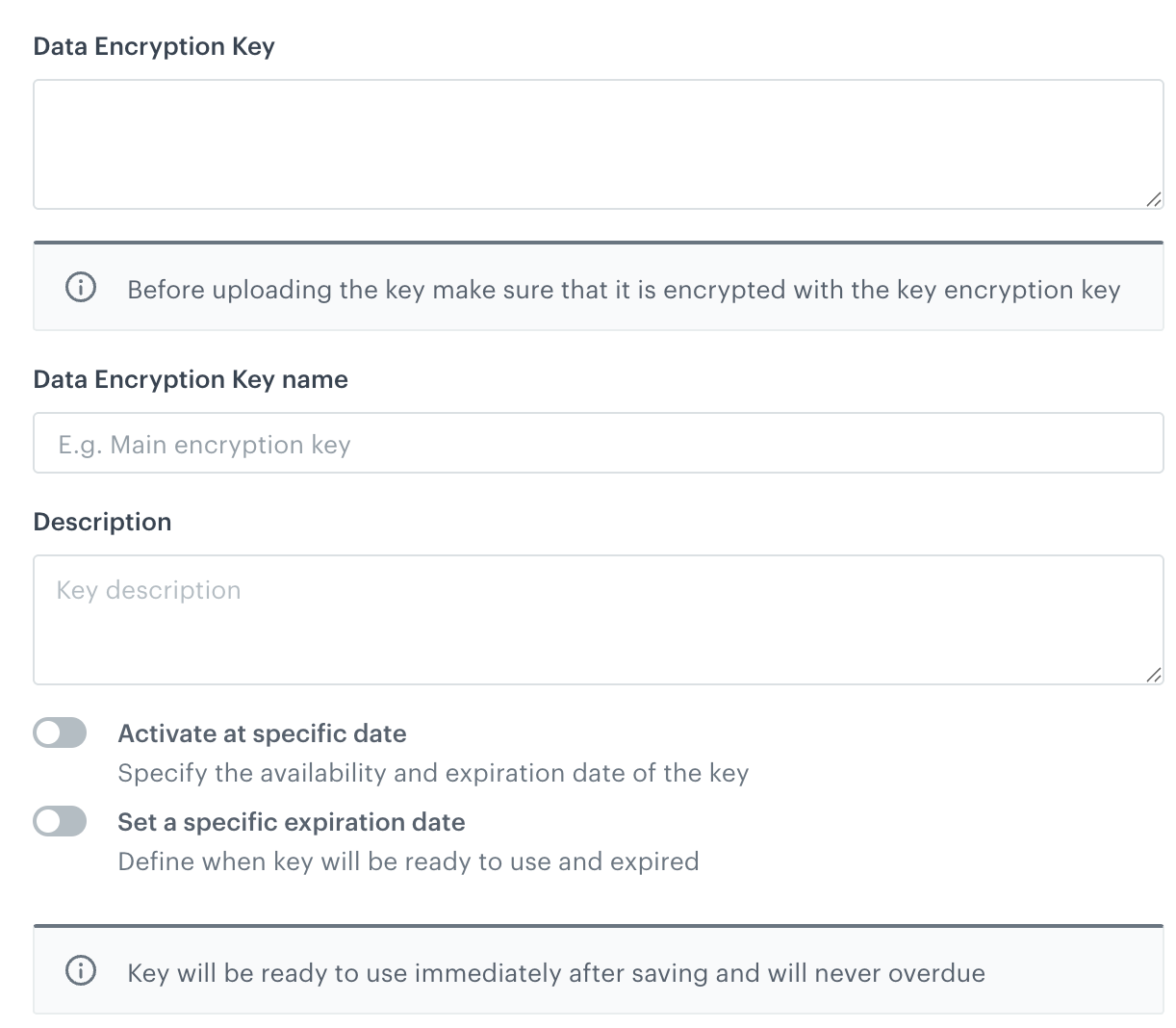
A blank form for creating a symmetric key - you selected Symmetric key (AES), click Download.
-
In Data Encryption Key:
- if you are adding an AES key, paste the wrapped key. Currently only 256 bit/32 byte secrets are supported.
- if you are adding RSA key, paste the public key.
-
In Data Encryption Key name, enter the name for your key for the purposes of identifying the key on the list of encryption keys.
-
In Description, enter the purpose of the encryption key.
-
Optionally, to define the activation and/or the expiration dates for the encryption key, enable Activate at specific date and/or Expire at specific date options, respectively. From the calendar, select the dates.
If you don’t provide:- the activation date, the key will be saved to be activated on the current date;
- the expiration date, the key will never expire.
-
Confirm the settings by clicking Apply.
Result: The key is saved and ready for use.
Adding a key version
- Go to Settings > Encryption keys.
- On the list of encryption keys, find the one to which you want to add a version.
- Next to the name of the encryption key, click
 .
. - From the dropdown list, click Add new version.
- Perform the steps from step 4 from the Adding encryption key section.
Important: You can only upload your key wrapped with key encryption key and optionally, define the activation and expiration dates for it.
Revoking a key
You can revoke a key, for instance, in the event of a key leak. Revoking a key will also revoke all of its versions. This action is irreversible and will break the integrations which use the key.
- Go to Settings > Encryption keys.
- On the list of encryption keys, find the one to which you want to revoke.
- Next to the name of the encryption key, click
 .
. - From the dropdown list, click Revoke.
Result: A pop-up appears. - Confirm the execution by clicking Yes, revoke.