"Encrypt Data" node
The Encrypt Data transformation lets you encrypt values in selected columns of a dataset. It enhances data security and confidentiality by encrypting sensitive information with AES-256 key using AES-GCM mode that is unreadable without the proper decryption key.
To decrypt the data, you can use the Decrypt data node or an external tool.
By using this transformation, you can safeguard your data and comply with privacy regulations while maintaining the integrity of your dataset.
Requirements
- You must have a user role with the following permission: Settings > Encryption keys > Read - To preview list of encryption keys, preview list of encryption keys in Encrypt Data and Decrypt Data nodes in Data Transformation;
- Add an encryption key in Synerise
- Your decryption tool/program must support the Synerise encryption format:
base64encode([IV] + [Encrypted Text] + [Authentication Tag]), whereIVis the initialization vector used to initiate the encryption algorithm andEncrypted Textis the result of an AES-GCM algorithm with a 256-bit secret.
Node configuration
-
Click the Encrypt Data node.
-
Click Add rule.
-
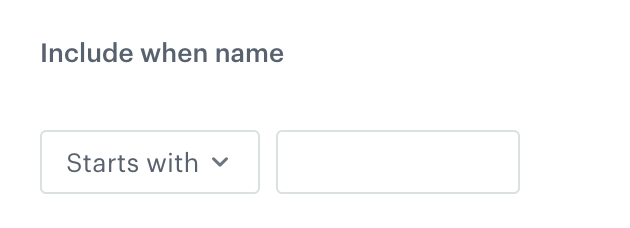
Select one of the Include options, by clicking the
 icon next to these:
icon next to these:- these - the default; it lets you select the columns in which you want to encrypt data.
- all except these - this option lets you select the columns in which you do NOT want to encrypt data. Values from the other columns will be encrypted as defined in the further steps.
-
Select columns to include/exclude (according to the Include setting above) in one of the following ways:
-
Select column - from the dropdown list, you can select the columns to be included or excluded from the transformation.
-
Add condition - you can create a dynamic condition which columns must meet to encrypt their values; for this purpose, you can use logical operators such as contain, starts with, ends with, and so on.
Important: You can’t combine dynamic conditions with the Include all except these option.
For further instructions, select one of the tabs below, depending on the option you have chosen in step 4.
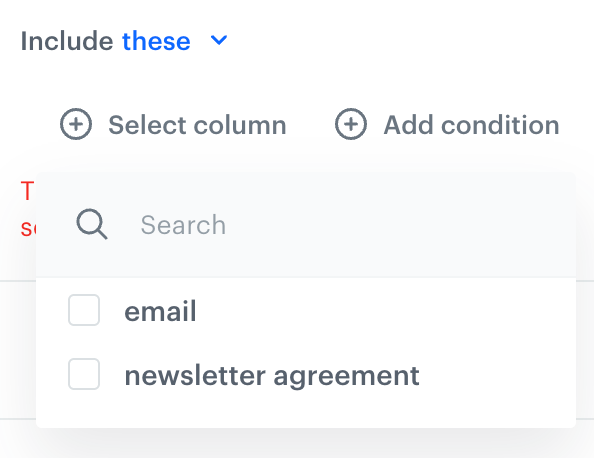
Select column option - From the dropdown list, select the first column whose values will be encrypted.
- To add more columns, click
 icon.
icon. - From the Encrypt data using dropdown list, select the key with which the data will be encrypted.
-
-
To add more rules, click Add rule and repeat steps from 3 to 5.
-
You can check the preview of the file after changes in the Output data tab.
-
Confirm the settings by clicking Apply.
Example of use
You can use the Encrypt Data node to encrypt a set of sensitive data. For example, you want to encrypt a column in a CSV file that contains email addresses of your customers. This example of use contains instructions how to create a transformation rule that encrypts a set of sensitive data. You can use this transformation rule in the Data Transformation node in a workflow that sends the file to an external source.
Before you proceed to creating a transformation rule that uses this node, ensure that you meet the requirements.
email,newsletter agreement
john.doe@example.com,yes
jane.smith@example.com,no
bob.johnson@example.com,yes
sara.white@example.com,yes
michael.brown@example.com,no- As the first node of the transformation rule, add Data Input.
- In the settings of the node, upload a file sample which imitates the structure of the source file (the one which will be used in a workflow which sends the actual file to your external source).
- Confirm the settings by clicking Apply.
- As the next node, add Encrypt Data.
- In the settings of the node, select the email column.
- From the Encrypt data using dropdown list, select the Synerise encryption key which will be used to encrypt data in this column.
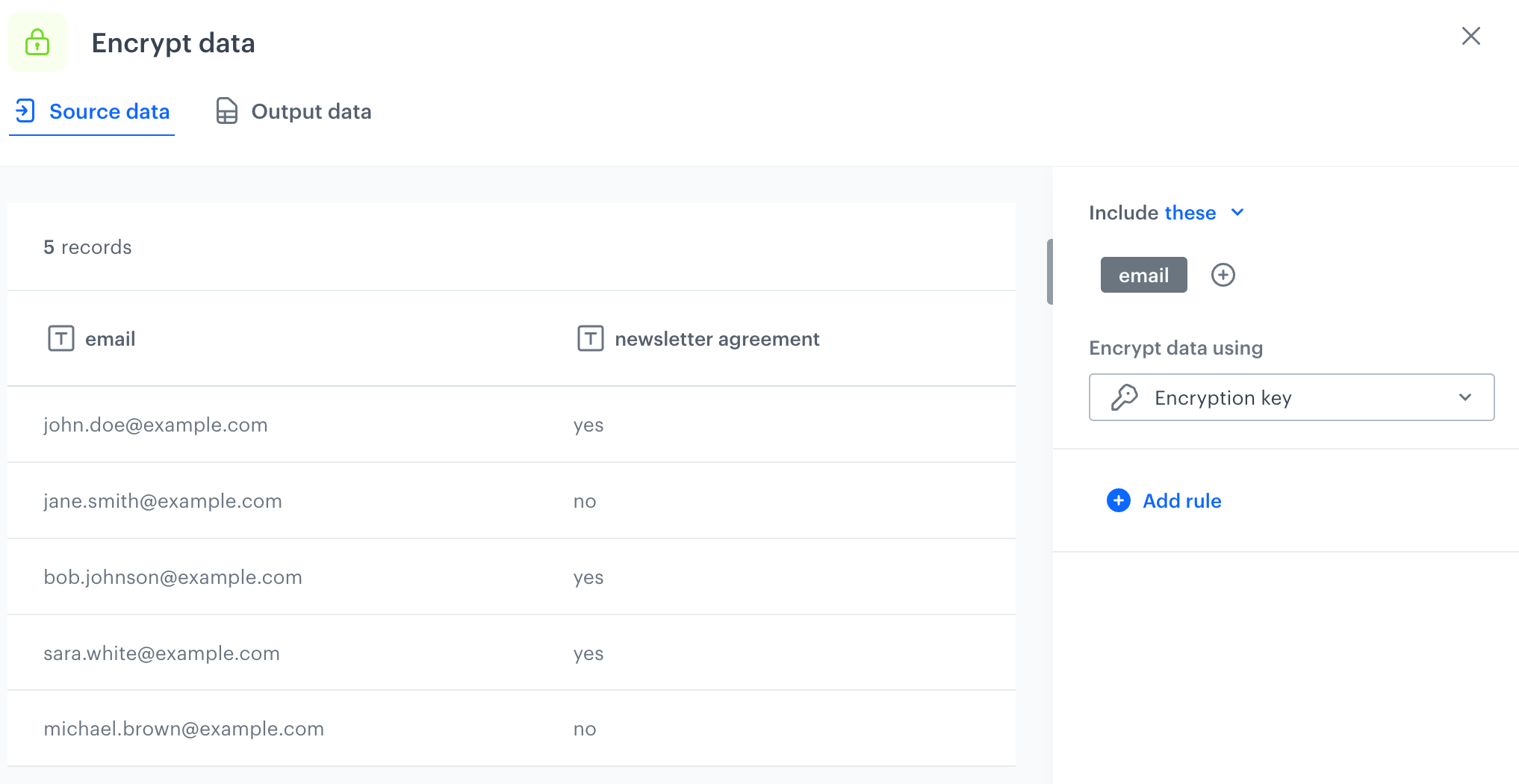
Configuration of the Encrypt Data node - Confirm the settings by clicking Apply.
- In the Output data tab in the Encrypt Data node, you can preview the results of the transformation in the node.
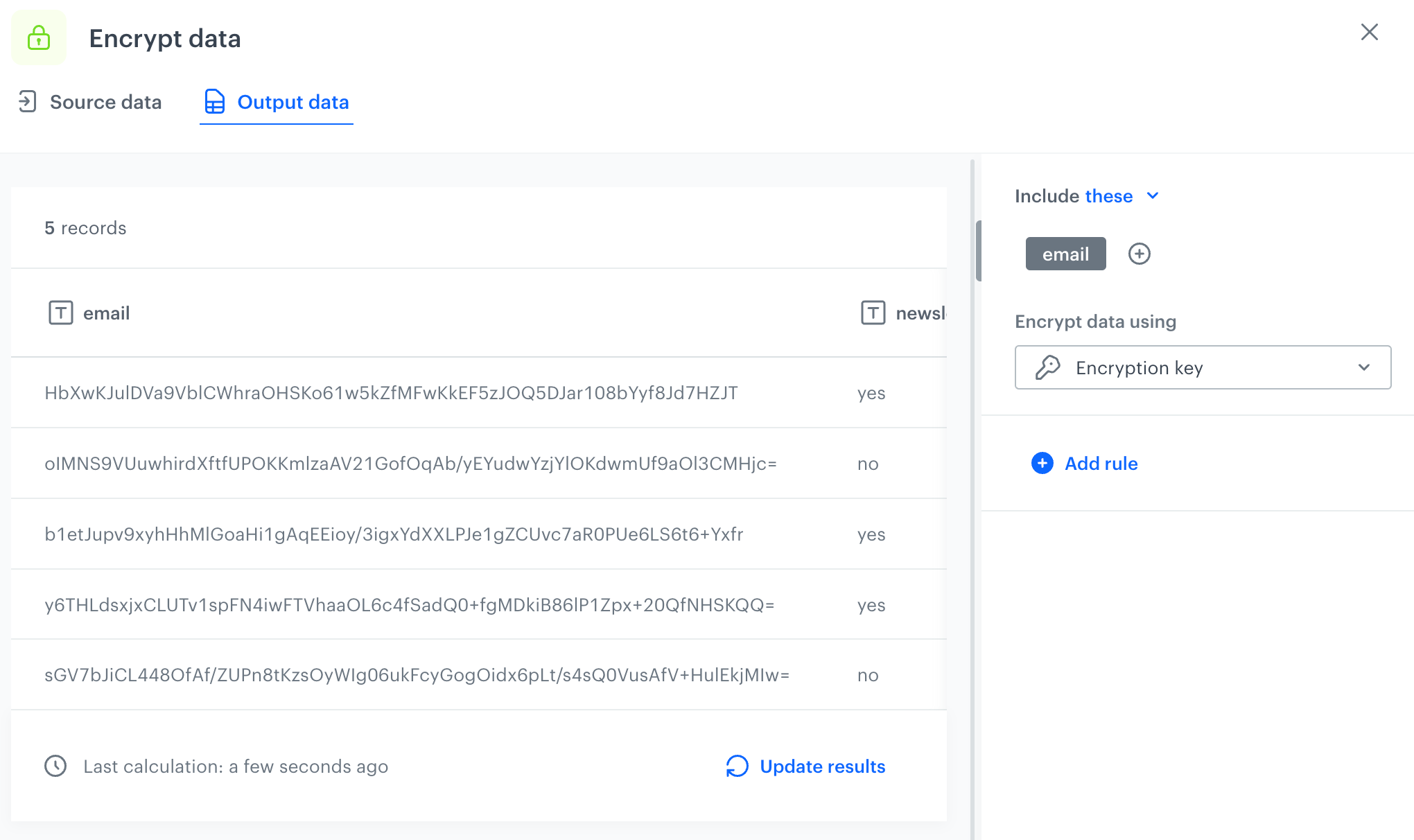
Output of the transformation performed within the Encrypt Data node - Add the Output Data node.
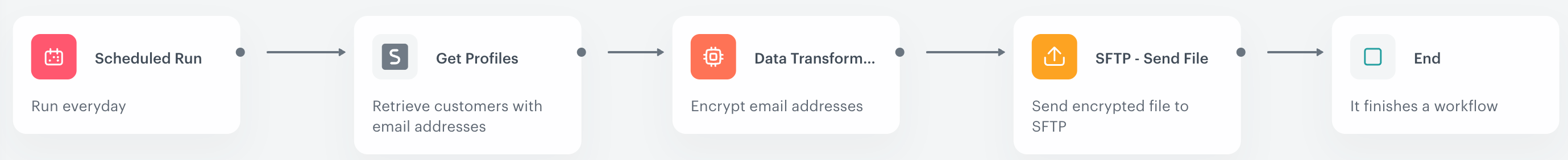
In the further steps, you can create a workflow that is triggered repeatedly, retrieves customers with email address assigned, encrypts email addresses with the transformation rule created in the previous steps, and sends the encrypted file with SFTP.